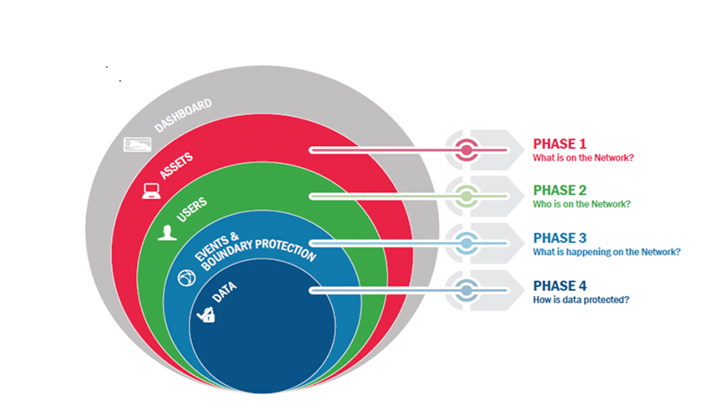
Continuous Diagnostics And Mitigation (CDM) Technical Implementation
Includes delivery of current and future CDM capabilities to Agencies by continuing the implementation of Phase 1 and 2 capabilities, extend to cloud and mobile, implement capabilities for network and physical security controls, ongoing
assessment and authorization, advanced data protections.
Continuous Diagnostics And Mitigation (CDM) Engineering Support
This included facilitating communications, identifying risks, driving the analysis of those risks, and ensuring mitigation
measures are put in place by refining operational processes within project scope included Change Management,
Incident Management, Release Management, and Configuration Management.
Independent Verification And Validation
Includes Security Operations Center (SOC) Support Services responsible to monitor, detect, analyze, mitigate, and respond
to cyber threats and adversarial activity across an Enterprise. Provide Independent Verification and Validation by
reviewing and performing analysis, communicating results, tracking V&V packages, and provide updates to be included
in audit reports.
Training And Support
Includes development, communication, and execution of Cybersecurity Training and awareness program’s strategy by
developing, maintaining, and supporting training materials for Cybersecurity Training Program to ensure an informed,
alert, and security-conscious workforce.